GIE
Encrypt and Decrypt
An Encrypt and Decrypt for files and folders for Windows, written in Python using AES.
[!CAUTION] Disclaimer: This tool was created for educational purposes only. I do not take any responsibility for the misuse of this tool.

Version
GIE V3.0
Features
Encrypt and decrypt your files and folders with AES, for any file, jpg, png, mp4, mp3, docx, pdf, etc...
IMPORTANT TO READ ALL
📦 Requirements
Subprocess
Hashlib
Cryptography
💻 Installation
Execute the commands according to your case (Win or Linux)
pyhon for windows
Clone or Download this Repository
#BATCH1git clone git@github.com:aiskoa/GIE.git 2
Change Directory
#BATCH1cd GIE 2
Run the setup.py file
#BATCH1python setup.py 2
OR install the dependencies manually
Run the project
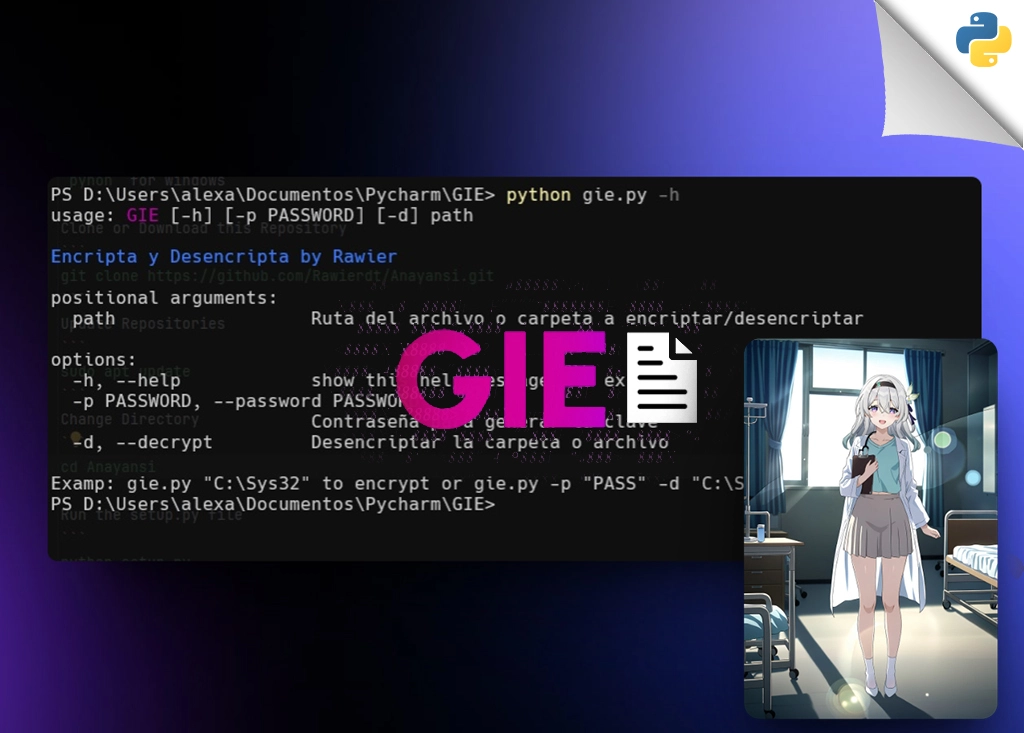
#BATCH1python gie.py -h 2
For Encrypt
Run -h for print the help/usage
#BATCH1python gie.py -h 2
To Encrypt a folder or file
- ! The path must be enclosed in quotes " "
For folders
#BATCH1python gie.py "C:\YOUR\FOLDER" 2
For only files
#BATCH1python gie.py "C:\YOUR\FILES.extension" 2
extension = jpg, png, mp3, mp4, docx, etc, etc...
- ! A message will appear that says: "Enter a password:"
! NOTE: The password cannot contain the characters $ and "
Example Output:
python gie.py "D:\Sam\Plugins\IP.exe"
Enter a password:
Note: The password will not be visible while you type it
Once the password is entered, it will start encrypting the files with the extension ".gie" and will generate a ".GKY" file, which is very important to decrypt your original file.
"GKY" is the extension of the file containing the key for decryption, along with the password provided.
! If you want to share the file with your colleague, you will need to provide him/her with three files, the .gie, the .GKY and the password.
For Decrypt
To Decrypt a folder or file
- ! The path and password must be enclosed in quotes " "
Run -d for decrypt
Run -p for set the password used previously
For folders
#BATCH1python gie.py -p "PASSWORD" -d "C:\YOUR\FOLDER" 2
For only files
#BATCH1python gie.py -p "PASSWORD" -d "C:\YOUR\FILES.extension.gie" 2
Example Output:
python gie.py -p "L1ñy*8Cv" -d "D:\Sam\Plugins\IP.exe"
The program will search if the .GKY file exists in the path provided and will try to decrypt the file with the password, if the password does not match the file will not decrypt or will decrypt corruptly, if the GKY does not exist, the program will throw an error message and will not be able to decrypt.
It is very important to save the .GKY and the PASSWORD very well.
Encrypt function
#PYTHON1def encrypt_file(input_file: str, password: str): 2 password_bytes = password.encode() # Convertir la contraseña a bytes 3 key_with_salt = generate_key(input_file, password_bytes) # Generar la clave utilizando bytes 4 if key_with_salt is None: 5 print(Fore.RED + "No se pudo generar la clave." + Style.RESET_ALL) 6 return 7 8 key = key_with_salt[16:] # Obtener la clave sin la sal 9 10 iv = os.urandom(16) 11 12 cipher = Cipher(algorithms.AES(key), modes.CBC(iv), backend=default_backend()) 13 encryptor = cipher.encryptor() 14 15 with open(input_file, "rb") as file_in: 16 data = file_in.read() 17 18 padded_data = data + b'\x00' * (-len(data) % 16) 19 encrypted_data = encryptor.update(padded_data) + encryptor.finalize() 20 21 output_file = input_file + ".gie" 22 with open(output_file, "wb") as file_out: 23 file_out.write(iv) 24 file_out.write(encrypted_data) 25 26 print(Fore.LIGHTMAGENTA_EX + f"Archivo ENCRIPTADO guardado como: {output_file}" + Style.RESET_ALL) 27 os.remove(input_file) 28
Decrypt function
#PYTHON1def decrypt_file(input_file: str, password: bytes): 2 base_file = os.path.splitext(os.path.basename(input_file))[0] # Remove all extensions 3 while "." in base_file: 4 base_file = os.path.splitext(base_file)[0] # Remove all extensions 5 # Add the .key extension to the base file name 6 key_file = os.path.join(os.path.dirname(input_file), base_file + ".GKY") 7 print(f"Buscando el archivo de la clave: {key_file}") # Print the name of the key file we are looking for 8 if os.path.exists(key_file): 9 with open(key_file, "rb") as f: 10 key_with_salt = f.read() 11 salt = key_with_salt[:16] # Get the stored salt 12 derived_key = hashlib.pbkdf2_hmac('sha256', password, salt, 100000, 32) 13 # print("La clave se recuperó con éxito.") 14 # print(f"Longitud de la clave: {len(derived_key)}") 15 # print(f"Longitud del salt: {len(salt)}") 16 17 with open(input_file, "rb") as file_in: 18 iv = file_in.read(16) 19 encrypted_data = file_in.read() 20 21 cipher = Cipher(algorithms.AES(derived_key), modes.CBC(iv), backend=default_backend()) 22 decryptor = cipher.decryptor() 23 24 decrypted_data = decryptor.update(encrypted_data) + decryptor.finalize() 25 unpadded_data = decrypted_data.rstrip(b'\\x00') 26 27 output_file = os.path.splitext(input_file)[0] 28 with open(output_file, "wb") as file_out: 29 file_out.write(unpadded_data) 30 31 print(Fore.LIGHTCYAN_EX + f"Archivo DESENCRIPTADO guardado como: {output_file}" + Style.RESET_ALL) 32 os.remove(input_file) 33 34 # Delete the key file after successful decryption 35 os.remove(key_file) 36 # print(f"Archivo de la clave {key_file} eliminado con éxito.") 37 38 else: 39 print(Fore.LIGHTRED_EX + "No se encontró la clave." + Style.RESET_ALL) 40 41
TODO List
-
Password check
-
AES
-
UI Menu
🤝 Contributing
Contributions, issues and feature requests are welcome! Feel free to check issues page.
❤️ Show your support
Give a ⭐️ if this project helped you!